Blog
Cryptography 101
06.08.2024

Whether in online banking, in our preferred messenger app, when surfing the world wide web or when using ID Austria (or the former Handy-Signatur): We encounter cryptography every day, even if we are not necessarily always aware of it. We often take it for granted that our data and our digital identity are protected, without knowing how this security can be guaranteed in the first place.
So if you still have a lot of question marks in your head when it comes to the topic of “data encryption”, we hope that our cryptography basics will help you.
Not quite so cryptic...
...is the meaning of the term “cryptography”, because its etymological origin already provides information about its core: the word is made up of the two ancient Greek words for hidden or secret („kryptós“) and write („gráphein“).
Accordingly, cryptography refers to the science and practice of encrypting information using various (sometimes mathematical) methods and techniques.
It generally pursues three core objectives: Ensuring ...
- confidentiality (only authorized persons should be able to know the content)
- integrity (content must be verifiably complete and unchanged)
- and authenticity (the originator(s) of the messages must be clearly identifiable)
...of information and data, which is why it also plays a decisive role in information security.
The fourth objective is non-repudiation The originator(s) of the data are not in a position to dispute their authorship. This objective also plays a central role in the qualified electronic signature.
Basic concepts of cryptography:
Encryption (encoding, ciphering)
This is the process by which information (“plaintext”) is converted into an incomprehensible form (“ciphertext”) using a defined key so that it cannot be read or understood by unauthorized persons.
Decryption (decoding, deciphering)
Is the process by which encrypted information is converted back into its original form so that it can be read by authorized persons.
Key
In cryptography, a “key” is the information that is used as a parameter for cryptographic algorithms. The key is therefore the central component for decrypting a ciphertext and thus obtaining the plaintext.
Symmetric encryption
In symmetric methods, all communication partners use the same (secret) key for both encryption and decryption.
The major disadvantage of symmetric methods is the use of the same key for encryption and decryption, as this key must be transmitted to the recipient of the message or data in addition to the encrypted information. The problem here is that a secure channel must be found to transmit the key, as the security of the process depends on the confidentiality of the key.
A simple example of this is the monoalphabetic substitution: Each letter of the plaintext is substituted into individual characters of the ciphertext using the key alphabet.

Example for the key of a monoalphabetic substitution.
The plaintext “SIMPLY SECURE” thus becomes the ciphertext “PXCMBD PLUGIL”.
One problem with monoalphabetic substitution is that certain letters or combinations occur statistically more frequently in specific languages, which makes the key quite easy to crack (especially for computers).
Asymmetric encryption
In asymmetric encryption, different keys are used to encrypt or decrypt the data.
Public key cryptography
The public key encryption is an asymmetric method in which two different but mathematically linked keys are used.
Each user has a key pair consisting of a public key and a private key. The public key can be freely distributed, while the private key must be kept secret.
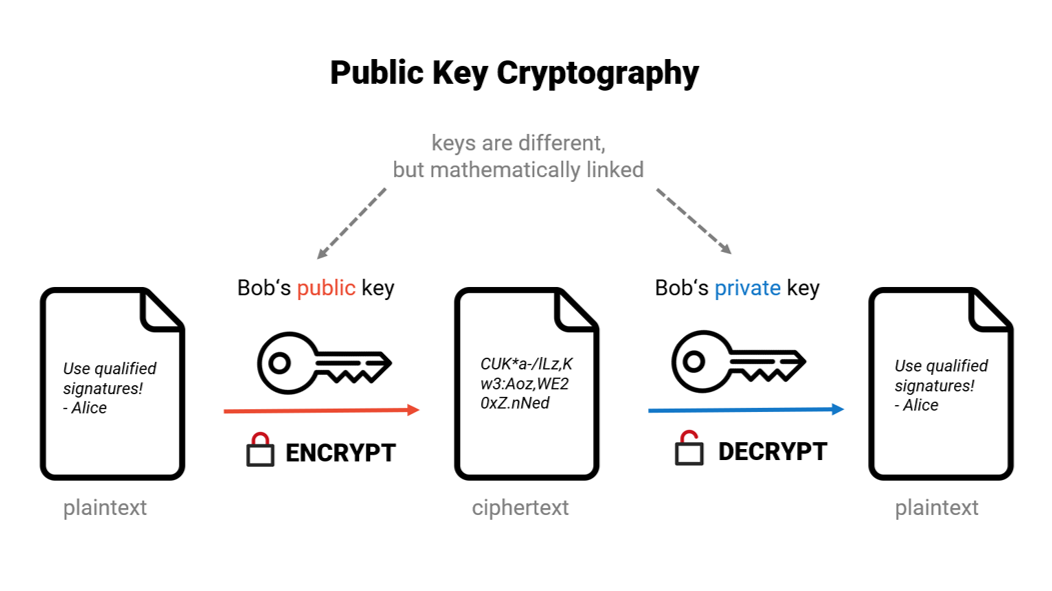
Example for the public key cryptography
Encryption of a message: A message that has been encrypted with the public key of a recipient can only be decrypted with the corresponding private key. This ensures that only the intended recipient can read the message.
Decrypting a message: The recipient uses their own private key to decrypt the encrypted message.
Creating a digital signature: The sender can sign a message with their own private key. This creates a digital signature that is attached to the message.
Verification of a digital signature: Anyone who has the sender's public key can verify the signature. This ensures that the message actually originates from the person in question and has not been altered.
Qualified electronic signatures in a nutshell
Several cryptographic processes are used, for example, when applying a qualified signature to a PDF document via the Signatur-Box or Hash2Sign:
Before the signature is applied, the so-called hash value of the document is calculated (using a hash algorithm). Only this hash value (and not the entire document) is transmitted to A-Trust for signing. (Objective: confidentiality)
The digital signature is calculated from the hash value of the data to be signed and the private key of the signatory. The signature can then be verified in the verification tool using the person's public key. (Objective: authenticity, non-repudiation)
If the document is subsequently changed, this hash value changes, which means that the signature can no longer be recognized as valid. (Objective: Integrity)
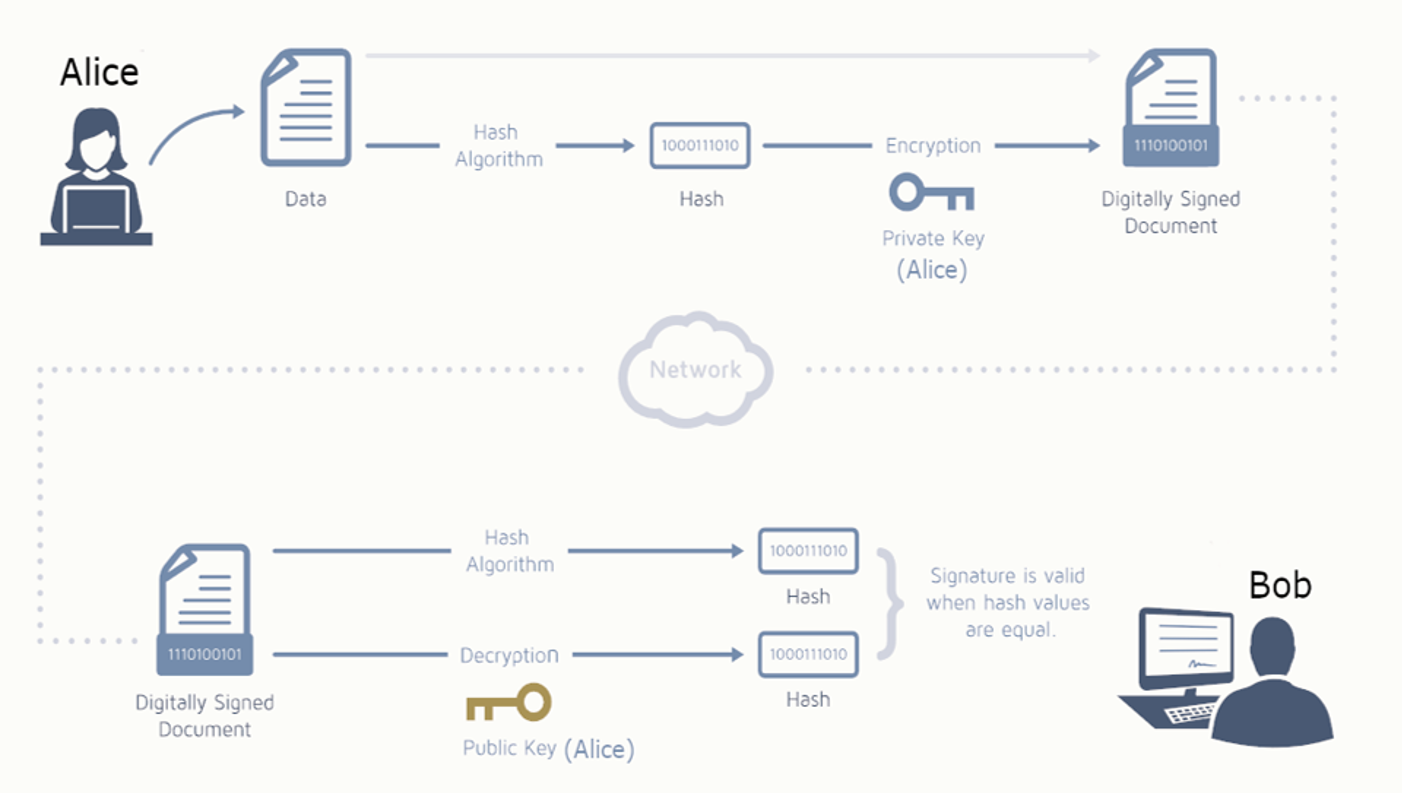
Example of the digital signature process for a document, including authentication of the signature.


